#PAM - Cloud and onPrem Protection
Comprehensive Privileged Access Management solutions designed for both the Cloud and onPrem enabling you to secure your most sensitive accounts, data and connections.
Prevent multiple current attack vectors
Obtain Compliance
Discover the full potential of JIT Access how it can help you prevent most of the top attack vectors while achieving compliance with Industry leading Cyber Insurance providers.
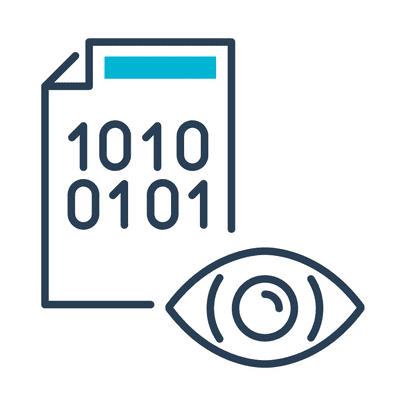
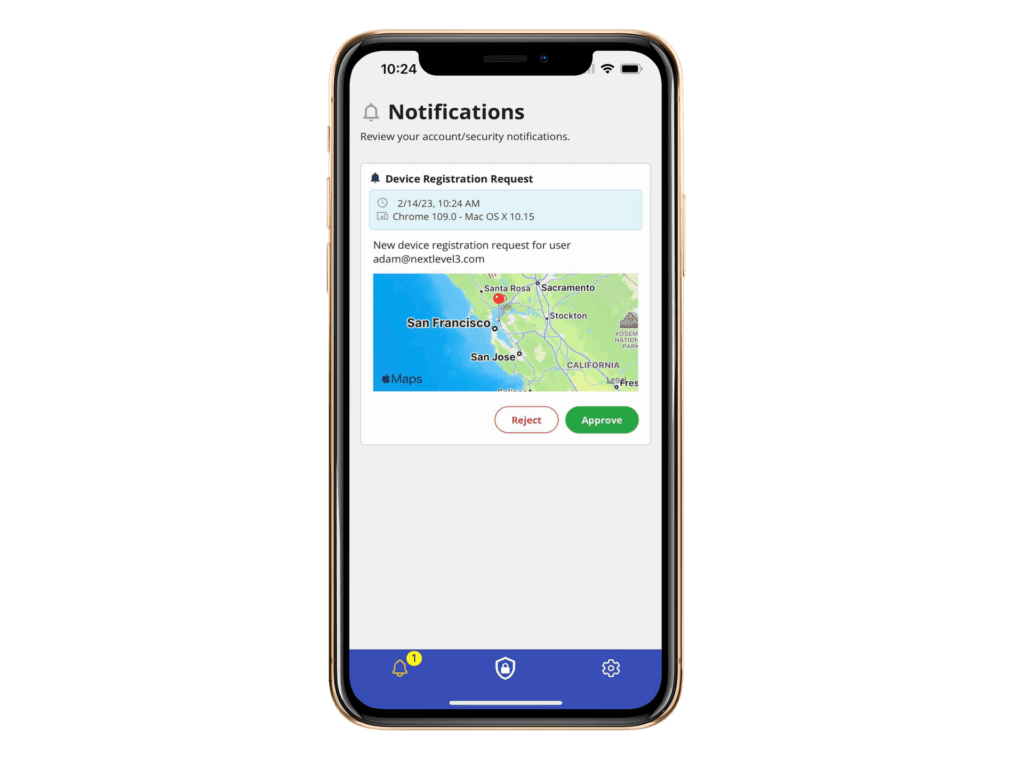
How it works
PAM protection enables you to secure your endpoints, workstations, remote connections, VPN connections and more with PAM modules designed for your specific environments.
Native support for Linux, Windows and MacOS operating systems.
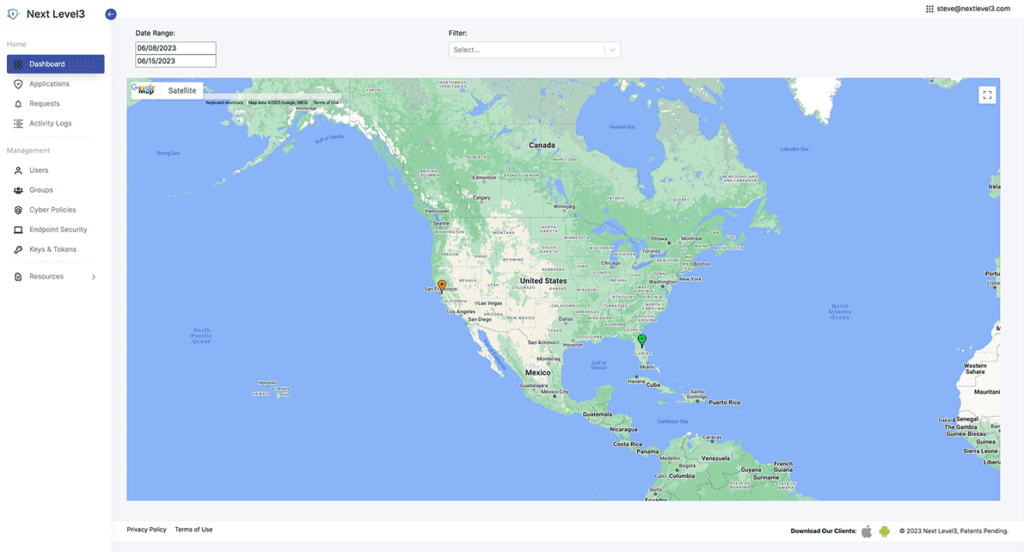
When users go to login, their locked and protected accounts require them to unlock their accounts, which they can only do after validating their biometrics to get access to their unique device key.
An endpoint security strategy is essential because every endpoint can be the starting point for an attack. With Next Level3 PAM (Pluggable Authentication Modules) you can rapidly deploy an effective passwordless solution throughout your organization.
Our PAM modules integrate seamlessly with JIT Access providing a native passwordless MFA solution for every environment.
- Workstations
- Legacy devices
- IOT Devices
- RDP connections
- SSH connections
- VPN Connections
Next Level3 does more! Extend your protection using JIT Access, JIT Policies and JIT Approvals to prevent a multitude of external and internal attack scenarios.

Automatic push attack aware protection without codes





Use your existing mobile or web FIDO2 supported devices





Why choose Next Level3?

JIT Access
Passwordless Identity seamlessly connected to your existing identity infrastructure.

JIT Policies
Redefine account control for your organization solving critical internal use cases.

JIT Approvals
Enable customized approvals for any application action preventing fraud and extending biometric protections into your application use cases.